Detect threats early; act now!
Be proactive with Info System Consultants’ cutting-edge detection solutions.
ISC DETECT
Secure your assets: Detect threats fast with us.
Empower your business with rapid, accurate threat detection, ensuring your operations stay safe and uninterrupted. Partner with us for cutting-edge solutions tailored to safeguard your customers’ trust and success.
- SIEM
- Intrusion Detection
- Anomaly Detection
- Threat Hunting
- Vulnerability Assessment
- 24/7 Monitoring and Alerting
Choose Info System Consultants for unmatched threat detection capabilities. Trust us to be your vigilant partner in cybersecurity, safeguarding your digital landscape and ensuring enduring business resilience and success.
Make Appointment
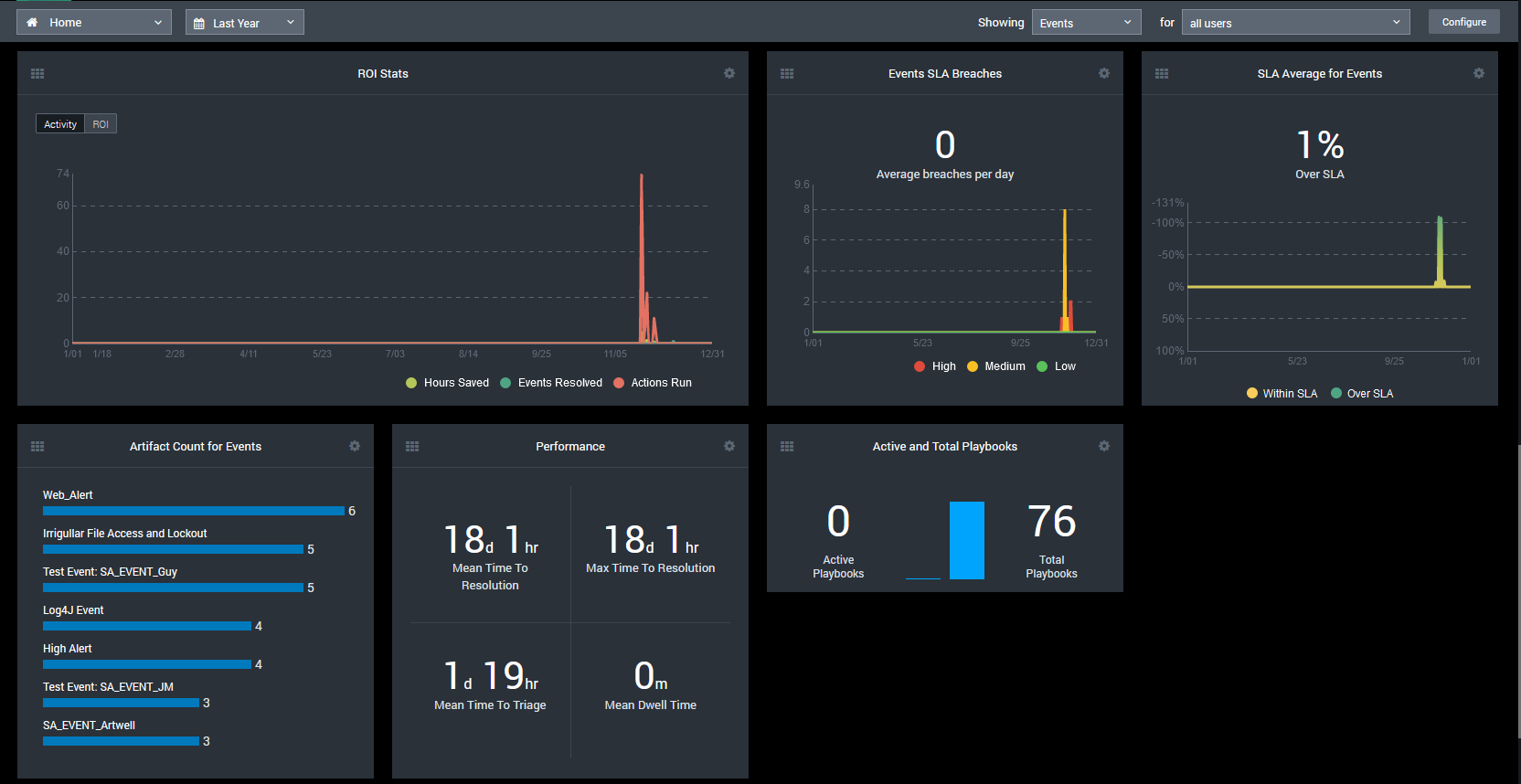
Stay Ahead of Cyber Threats with Advanced Detection
58% of cyber attacks target SMBs. Elevate your defense with our Detection solutions. Identify threats early, secure your business’s digital future.
Discover Detection – Enhance Your Security Now!
FAQ
Popular Question
Discover how Detect provides advanced, user-friendly cybersecurity, differentiating real threats from normal activity for businesses of all sizes.
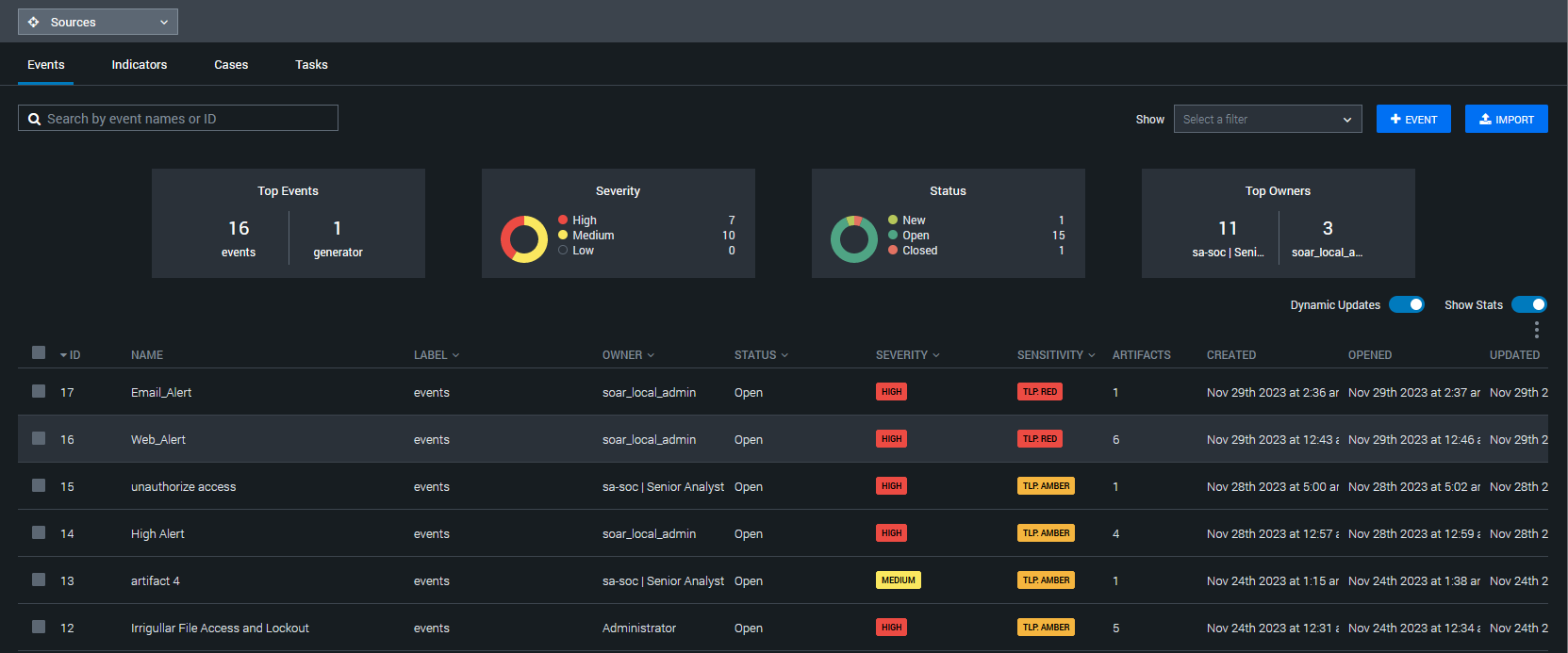
ISC Detect is a cutting-edge cybersecurity tool focused on the early identification and understanding of digital threats. It employs real-time monitoring, anomaly detection, and advanced threat intelligence to identify potential security breaches swiftly and accurately. This proactive approach helps businesses pre-emptively address threats before they escalate.
ISC Detect utilizes sophisticated algorithms and machine learning to analyze network behaviour patterns. It establishes a baseline of normal activity and then continuously monitors for deviations from this norm. By identifying anomalies and unusual patterns, it can effectively distinguish between benign activities and potential security threats.
Yes, ISC Detect is designed to be user-friendly and efficient, making it suitable for businesses of all sizes, including those without specialized IT security teams. Its automated alert systems ensure that businesses can effectively monitor their cybersecurity status without needing extensive technical expertise.

